UID1
性别保密
注册时间2013-7-10
最后登录1970-1-1
回帖0
在线时间 小时
精华
SB
威望
随币
 成长值: 52050 成长值: 52050
|
马上注册,结交更多好友,享用更多功能,让你轻松玩转社区。
您需要 登录 才可以下载或查看,没有账号?立即注册
x
<h2 style="text-align: center; font-size: 1.3em; padding-top: 15px; padding-bottom: 5px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><font><font style="background-color: white;" class="goog-text-highlight">
 <br></font></font></h2><h2 style="font-size: 1.3em; padding-top: 15px; padding-bottom: 5px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><font><font style="background-color: white;" class="">埃及黑客易卜拉欣Hegazy发现了一个关键的雅虎SQL注入漏洞被利用来远程执行代码和特权提升。</font></font></h2><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>我的读者都很清楚,埃及黑客 </font><a title="eg.linkedin.com/in/ebrahimhegazy/it" href="http://securityaffairs.co/wordpress/28475/hacking/eg.linkedin.com/in/ebrahimhegazy/it" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font>易卜拉欣Hegazy</font></a><font>,他是一个伟大的安全专家和我的一个朋友,其中披露最流行的网络服务,包括微软,雅虎和桔子许多严重的缺陷。</font></font> <a title="eg.linkedin.com/in/ebrahimhegazy/it" href="http://securityaffairs.co/wordpress/28475/hacking/eg.linkedin.com/in/ebrahimhegazy/it" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font></font></a><font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>最后发现的网络安全专家是一个</font></font><a title="Ponemon研究 - SQL注入攻击的组织太危险" href="http://securityaffairs.co/wordpress/24094/cyber-crime/ponemon-sql-injection-attacks.html" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font>SQL注入</font></font></a> <font><font> 的,可能被攻击者所利用雅虎的服务</font></font><a title="德国研究人员发现的远程代码执行漏洞在eBay的子域名" href="http://securityaffairs.co/wordpress/20461/hacking/ebay-remote-code-execution.html" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font>远程执行代码</font></font></a><font><font>,并升级为超级用户权限,对雅虎的服务器之一。</font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>正如他在解释</font></font><a title="http://www.sec-down.com/wordpress/?p=494" href="http://www.sec-down.com/wordpress/?p=494" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font>的博客文章</font></font></a><font><font>,易卜拉欣开始了他的分析</font></font><span id="9191cf63-ca35-4761-9606-67754a817d4f" class="GINGER_SOFTWARE_mark"><font><font>,从</font></font></span><font><font>域名:http://innovationjockeys.yahoo.net/,尤其是当他检查的HTTP POST请求,他发现了一些可以被利用的SQL注入攻击:</font></font></span></p><pre style="font-size: 1em; margin-top: 10px; margin-bottom: 10px; padding: 1em 10px; overflow: auto; color: rgb(0, 0, 0); line-height: 26.399999618530273px;"><span style="background-color: white;"><em><font><font>http://innovationjockeys.net/tictac_chk_req.php </font></font></em>
<br></font></font></h2><h2 style="font-size: 1.3em; padding-top: 15px; padding-bottom: 5px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><font><font style="background-color: white;" class="">埃及黑客易卜拉欣Hegazy发现了一个关键的雅虎SQL注入漏洞被利用来远程执行代码和特权提升。</font></font></h2><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>我的读者都很清楚,埃及黑客 </font><a title="eg.linkedin.com/in/ebrahimhegazy/it" href="http://securityaffairs.co/wordpress/28475/hacking/eg.linkedin.com/in/ebrahimhegazy/it" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font>易卜拉欣Hegazy</font></a><font>,他是一个伟大的安全专家和我的一个朋友,其中披露最流行的网络服务,包括微软,雅虎和桔子许多严重的缺陷。</font></font> <a title="eg.linkedin.com/in/ebrahimhegazy/it" href="http://securityaffairs.co/wordpress/28475/hacking/eg.linkedin.com/in/ebrahimhegazy/it" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font></font></a><font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>最后发现的网络安全专家是一个</font></font><a title="Ponemon研究 - SQL注入攻击的组织太危险" href="http://securityaffairs.co/wordpress/24094/cyber-crime/ponemon-sql-injection-attacks.html" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font>SQL注入</font></font></a> <font><font> 的,可能被攻击者所利用雅虎的服务</font></font><a title="德国研究人员发现的远程代码执行漏洞在eBay的子域名" href="http://securityaffairs.co/wordpress/20461/hacking/ebay-remote-code-execution.html" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font>远程执行代码</font></font></a><font><font>,并升级为超级用户权限,对雅虎的服务器之一。</font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>正如他在解释</font></font><a title="http://www.sec-down.com/wordpress/?p=494" href="http://www.sec-down.com/wordpress/?p=494" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font>的博客文章</font></font></a><font><font>,易卜拉欣开始了他的分析</font></font><span id="9191cf63-ca35-4761-9606-67754a817d4f" class="GINGER_SOFTWARE_mark"><font><font>,从</font></font></span><font><font>域名:http://innovationjockeys.yahoo.net/,尤其是当他检查的HTTP POST请求,他发现了一些可以被利用的SQL注入攻击:</font></font></span></p><pre style="font-size: 1em; margin-top: 10px; margin-bottom: 10px; padding: 1em 10px; overflow: auto; color: rgb(0, 0, 0); line-height: 26.399999618530273px;"><span style="background-color: white;"><em><font><font>http://innovationjockeys.net/tictac_chk_req.php </font></font></em>
<em><strong><font><font>邮编:</font></font></strong></em>
<em><font><font> F_ID = 9631</font></font></em></span></pre><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><font><font style="background-color: white;">经过几次人工测试,并配合使用的SqlMap的,黑客证实了雅虎的系统存在缺陷的存在:</font></font></p><pre style="font-size: 1em; margin-top: 10px; margin-bottom: 10px; padding: 1em 10px; overflow: auto; color: rgb(0, 0, 0); line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>http://innovationjockeys.net/tictac_chk_req.php
</font></font><strong><font><font>邮编:</font></font></strong><font><font>
F_ID = -9631'OR(2777 = 2777 </font></font><span id="37101007-9b4f-4d0e-a36c-8f714053cf26" class="GINGER_SOFTWARE_mark"><font><font>)</font></font></span><font><font>#</font></font></span></pre><pre style="font-size: 1em; margin-top: 10px; margin-bottom: 10px; padding: 1em 10px; overflow: auto; color: rgb(0, 0, 0); line-height: 26.399999618530273px;"><span style="background-color: white;"><strong><font><font>可用数据库:</font></font></strong>
<strong><font><font></font></font></strong><font><font> INFORMATION_SCHEMA
</font></font><strong><font><font></font></font></strong><font><font>创新******* #Hiding </font></font><span id="7e2f2129-6a8d-49c2-9521-eb20f364112d" class="GINGER_SOFTWARE_mark"><font><font>数据库名称</font></font></span><font><font>。雅虎的隐私
</font></font><strong><font><font></font></font></strong><font><font>网****</font></font></span></pre><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><font><font style="background-color: white;">这是一个笑话专家来读取存储在SQL注入攻击数据库中的数据,在这一点上易卜拉欣曾经收集的管理员凭据从数据库中他能够对它们进行解码,尽管它被编码为Base64编码。</font></font></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="0f502ba9-bddd-4467-a108-d39de4a18799" class="GINGER_SOFTWARE_mark"><font><font>易卜拉欣</font></font></span><font><font>使用的凭据访问管理面板,他发现</font></font></span></p><blockquote style="margin-top: 20px; margin-bottom: 20px; margin-left: 20px; padding-left: 20px; border-left-width: 3px; border-left-style: solid; border-left-color: rgb(203, 202, 200); color: rgb(102, 102, 102); font-style: italic; line-height: 1.5em; font-family: Arial, Helvetica, sans-serif; font-size: 13px;"><p style="font-size: 1em; margin-bottom: 10px;"><em><font><font style="background-color: white;">1管理面板上发现:HTTP://innovationjockeys.yahoo.net/admin/</font></font></em></p><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><font><font>2 -我</font></font><span id="562b354b-82a5-4620-8e85-af7aea3a4402" class="GINGER_SOFTWARE_mark"><span id="0515ea70-a49f-47c4-b612-30dcd553bb0f" class="GINGER_SOFTWARE_mark"><span id="06c284a6-d29b-4cea-99f0-b5aec4300b3a" class="GINGER_SOFTWARE_mark"><span id="bf5d5950-3159-48e2-99f3-8f24b984f3ee" class="GINGER_SOFTWARE_mark"><span id="218ed078-50d1-4a65-abef-8add8bff5b14" class="GINGER_SOFTWARE_mark"><span id="00cc572b-cbf0-4d6a-9418-3dc3a5e6ac0d" class="GINGER_SOFTWARE_mark"><span id="90aa9afb-38d2-4f0f-b485-82f92c099e39" class="GINGER_SOFTWARE_mark"><span id="33ecbf10-b00d-460d-bd32-aaeb0a3a9544" class="GINGER_SOFTWARE_mark"><font><font>发现</font></font></span></span></span></span></span></span></span></span><font><font>存储在数据库管理员发布密码,它被编码为</font></font><strong><font><font>Base64的编码</font></font></strong> <img class="wp-smiley" src="http://www.sec-down.com/wordpress/wp-includes/images/smilies/icon_biggrin.gif" alt=":D" title="雅虎的SQL注入漏洞允许执行和权限远程代码scalation"></em></p></blockquote><p style="text-align: center; font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><a href="http://securityaffairs.co/wordpress/wp-content/uploads/2014/09/SQL-Injection-Yahoo-1.png" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold; background-color: white;">
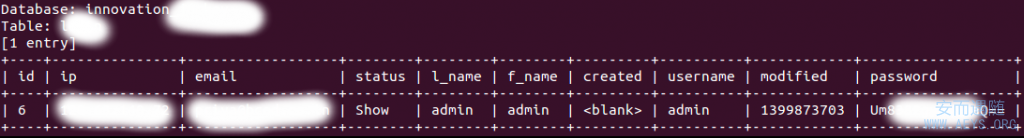 </a></p><blockquote style="margin-top: 20px; margin-bottom: 20px; margin-left: 20px; padding-left: 20px; border-left-width: 3px; border-left-style: solid; border-left-color: rgb(203, 202, 200); color: rgb(102, 102, 102); font-style: italic; line-height: 1.5em; font-family: Arial, Helvetica, sans-serif; font-size: 13px;"><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><font><font>不错,我已经解码的管理员密码,登录</font></font><span id="ff03e7aa-a21b-42c3-b6d4-73ab156961ee" class="GINGER_SOFTWARE_mark"><span id="2a779fa1-7524-4694-ad64-4949763a9764" class="GINGER_SOFTWARE_mark"><span id="c7666dea-c441-4a00-b297-51ea8ce77636" class="GINGER_SOFTWARE_mark"><span id="bef568e3-18d3-411c-a0c5-a53660bab1eb" class="GINGER_SOFTWARE_mark"><span id="1f2a7581-5763-4a05-97ce-317cc413e78d" class="GINGER_SOFTWARE_mark"><span id="298a31e8-50b4-488a-a4eb-0313b391df26" class="GINGER_SOFTWARE_mark"><span id="f81d8a41-758f-475c-98db-f33a70309b9f" class="GINGER_SOFTWARE_mark"><span id="7edcee33-ed16-408c-8df0-227d588cb2b9" class="GINGER_SOFTWARE_mark"><font><font>到收藏夹</font></font></span></span></span></span></span></span></span></span><font><font>管理面板。</font></font></em></p></blockquote><p style="text-align: center; font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><a href="http://securityaffairs.co/wordpress/wp-content/uploads/2014/09/SQL-Injection-Yahoo-2.png" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold; background-color: white;">
</a></p><blockquote style="margin-top: 20px; margin-bottom: 20px; margin-left: 20px; padding-left: 20px; border-left-width: 3px; border-left-style: solid; border-left-color: rgb(203, 202, 200); color: rgb(102, 102, 102); font-style: italic; line-height: 1.5em; font-family: Arial, Helvetica, sans-serif; font-size: 13px;"><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><font><font>不错,我已经解码的管理员密码,登录</font></font><span id="ff03e7aa-a21b-42c3-b6d4-73ab156961ee" class="GINGER_SOFTWARE_mark"><span id="2a779fa1-7524-4694-ad64-4949763a9764" class="GINGER_SOFTWARE_mark"><span id="c7666dea-c441-4a00-b297-51ea8ce77636" class="GINGER_SOFTWARE_mark"><span id="bef568e3-18d3-411c-a0c5-a53660bab1eb" class="GINGER_SOFTWARE_mark"><span id="1f2a7581-5763-4a05-97ce-317cc413e78d" class="GINGER_SOFTWARE_mark"><span id="298a31e8-50b4-488a-a4eb-0313b391df26" class="GINGER_SOFTWARE_mark"><span id="f81d8a41-758f-475c-98db-f33a70309b9f" class="GINGER_SOFTWARE_mark"><span id="7edcee33-ed16-408c-8df0-227d588cb2b9" class="GINGER_SOFTWARE_mark"><font><font>到收藏夹</font></font></span></span></span></span></span></span></span></span><font><font>管理面板。</font></font></em></p></blockquote><p style="text-align: center; font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><a href="http://securityaffairs.co/wordpress/wp-content/uploads/2014/09/SQL-Injection-Yahoo-2.png" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold; background-color: white;">
 </a></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><font><font style="background-color: white;">在这一点上,专家试图引发远程代码Executionuploading他的内容。</font></font></p><blockquote style="margin-top: 20px; margin-bottom: 20px; margin-left: 20px; padding-left: 20px; border-left-width: 3px; border-left-style: solid; border-left-color: rgb(203, 202, 200); color: rgb(102, 102, 102); font-style: italic; line-height: 1.5em; font-family: Arial, Helvetica, sans-serif; font-size: 13px;"><p style="font-size: 1em; margin-bottom: 10px;"><span style="background-color: white;"><em><font><font>“这么说,我已经找到</font></font><span id="4ba93b3a-fb14-4c44-a43c-2e956c6b1060" class="GINGER_SOFTWARE_mark"><span id="bca3fce9-25e8-4ddc-aa37-7729a12515a2" class="GINGER_SOFTWARE_mark"><span id="bb059d95-2ce8-489b-93e5-2a2a3a0eae67" class="GINGER_SOFTWARE_mark"><span id="a538e534-2b11-42cc-bb42-5cba4520f1cd" class="GINGER_SOFTWARE_mark"><span id="fa58d105-897f-4976-9e90-3910f2ce9bb4" class="GINGER_SOFTWARE_mark"><span id="ebe89bad-9357-42af-95a4-dbf043fb7e6e" class="GINGER_SOFTWARE_mark"><span id="9d2e3b73-b874-4352-98cf-00fce4fc474a" class="GINGER_SOFTWARE_mark"><span id="6ad5c01d-b3cd-410f-bdb7-008be485e96e" class="GINGER_SOFTWARE_mark"><font><font>à</font></font></span></span></span></span></span></span></span></span><font><font>上传页面,但与上传文件后“的phpinfo </font><span id="0abff33e-9b19-4b81-88c6-351609db7406" class="GINGER_SOFTWARE_mark"><span id="2aa002db-1fa3-4426-a63f-58a77b803238" class="GINGER_SOFTWARE_mark"><span id="782a87f0-4def-4e77-848c-bb0f80df189c" class="GINGER_SOFTWARE_mark"><span id="2f8c8b2c-1e54-4cc4-99ef-917deacc62b5" class="GINGER_SOFTWARE_mark"><span id="d1ee8e0b-a182-47b3-ae3e-aec6e3c4d4d5" class="GINGER_SOFTWARE_mark"><span id="ba9813f9-adcb-456c-863f-3d8a1274aee2" class="GINGER_SOFTWARE_mark"><span id="5b2f2d5e-5493-4e91-9643-97dfa67ac4f2" class="GINGER_SOFTWARE_mark"><span id="7a99f861-ef68-4a9c-b209-c4cbf5c76989" class="GINGER_SOFTWARE_mark"><font>(</font></span></span></span></span></span></span></span></span><font>);“功能的内容,</font></font> <span id="0abff33e-9b19-4b81-88c6-351609db7406" class="GINGER_SOFTWARE_mark"><span id="2aa002db-1fa3-4426-a63f-58a77b803238" class="GINGER_SOFTWARE_mark"><span id="782a87f0-4def-4e77-848c-bb0f80df189c" class="GINGER_SOFTWARE_mark"><span id="2f8c8b2c-1e54-4cc4-99ef-917deacc62b5" class="GINGER_SOFTWARE_mark"><span id="d1ee8e0b-a182-47b3-ae3e-aec6e3c4d4d5" class="GINGER_SOFTWARE_mark"><span id="ba9813f9-adcb-456c-863f-3d8a1274aee2" class="GINGER_SOFTWARE_mark"><span id="5b2f2d5e-5493-4e91-9643-97dfa67ac4f2" class="GINGER_SOFTWARE_mark"><span id="7a99f861-ef68-4a9c-b209-c4cbf5c76989" class="GINGER_SOFTWARE_mark"><font></font></span></span></span></span></span></span></span></span><font></font></em><br><em><font><font>我发现我上传的文件被命名为:page_d03b042780c5071521366edc01e52d3d </font></font><span id="aecd5cd8-2164-490b-a4d3-879a54e22ce9" class="GINGER_SOFTWARE_mark"><span id="182bb827-5d4b-42f5-b5d0-6ff8171d3c42" class="GINGER_SOFTWARE_mark"><span id="d1dc8af8-e35d-433c-b93b-4e74c57fc598" class="GINGER_SOFTWARE_mark"><span id="4446587a-b876-4c0f-9f92-0c30b74ea723" class="GINGER_SOFTWARE_mark"><span id="33aa4f07-c280-4404-bb9a-d4aecfd54528" class="GINGER_SOFTWARE_mark"><span id="2af7e5e5-2933-4c40-9b40-51abe0e9f219" class="GINGER_SOFTWARE_mark"><span id="a3da4687-fb7d-4220-adb8-7939eeef033a" class="GINGER_SOFTWARE_mark"><span id="75efb129-ade2-4b2d-ba2b-e38743c1f894" class="GINGER_SOFTWARE_mark"><font><font>。</font></font></span></span></span></span></span></span></span></span> <font><font> XRDS + XML </font><span id="60948e07-2cf5-4122-a833-0aef219698d3" class="GINGER_SOFTWARE_mark"><span id="e2787126-d253-4f0c-9089-7398b761fcf3" class="GINGER_SOFTWARE_mark"><span id="bff7926f-3e04-4c35-a9df-e028f9a56fd7" class="GINGER_SOFTWARE_mark"><span id="6bea52a7-9e26-4980-b550-24dd2371ff5e" class="GINGER_SOFTWARE_mark"><font>,而不是</font></span></span></span></span><font>被page_d03b042780c5071521366edc01e52d3d.php </font><span id="24c15c8d-354f-4237-86c3-087c5ce47a37" class="GINGER_SOFTWARE_mark"><font>?!“国在博客中Hibrahim。</font></span></font> <span id="60948e07-2cf5-4122-a833-0aef219698d3" class="GINGER_SOFTWARE_mark"><span id="e2787126-d253-4f0c-9089-7398b761fcf3" class="GINGER_SOFTWARE_mark"><span id="bff7926f-3e04-4c35-a9df-e028f9a56fd7" class="GINGER_SOFTWARE_mark"><span id="6bea52a7-9e26-4980-b550-24dd2371ff5e" class="GINGER_SOFTWARE_mark"><font></font></span></span></span></span><font></font><span id="24c15c8d-354f-4237-86c3-087c5ce47a37" class="GINGER_SOFTWARE_mark"><font></font></span></em></span></p></blockquote><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="528f9d50-1474-40c6-926e-32deb4141b7e" class="GINGER_SOFTWARE_mark"><font><font>检查</font></font></span><font><font> 3篇的要求,专家发现了问题的原因,在“内容类型”头!</font></font></span></p><p style="text-align: center; font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><a href="http://securityaffairs.co/wordpress/wp-content/uploads/2014/09/SQL-Injection-Yahoo-3.png" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold; background-color: white;">
</a></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><font><font style="background-color: white;">在这一点上,专家试图引发远程代码Executionuploading他的内容。</font></font></p><blockquote style="margin-top: 20px; margin-bottom: 20px; margin-left: 20px; padding-left: 20px; border-left-width: 3px; border-left-style: solid; border-left-color: rgb(203, 202, 200); color: rgb(102, 102, 102); font-style: italic; line-height: 1.5em; font-family: Arial, Helvetica, sans-serif; font-size: 13px;"><p style="font-size: 1em; margin-bottom: 10px;"><span style="background-color: white;"><em><font><font>“这么说,我已经找到</font></font><span id="4ba93b3a-fb14-4c44-a43c-2e956c6b1060" class="GINGER_SOFTWARE_mark"><span id="bca3fce9-25e8-4ddc-aa37-7729a12515a2" class="GINGER_SOFTWARE_mark"><span id="bb059d95-2ce8-489b-93e5-2a2a3a0eae67" class="GINGER_SOFTWARE_mark"><span id="a538e534-2b11-42cc-bb42-5cba4520f1cd" class="GINGER_SOFTWARE_mark"><span id="fa58d105-897f-4976-9e90-3910f2ce9bb4" class="GINGER_SOFTWARE_mark"><span id="ebe89bad-9357-42af-95a4-dbf043fb7e6e" class="GINGER_SOFTWARE_mark"><span id="9d2e3b73-b874-4352-98cf-00fce4fc474a" class="GINGER_SOFTWARE_mark"><span id="6ad5c01d-b3cd-410f-bdb7-008be485e96e" class="GINGER_SOFTWARE_mark"><font><font>à</font></font></span></span></span></span></span></span></span></span><font><font>上传页面,但与上传文件后“的phpinfo </font><span id="0abff33e-9b19-4b81-88c6-351609db7406" class="GINGER_SOFTWARE_mark"><span id="2aa002db-1fa3-4426-a63f-58a77b803238" class="GINGER_SOFTWARE_mark"><span id="782a87f0-4def-4e77-848c-bb0f80df189c" class="GINGER_SOFTWARE_mark"><span id="2f8c8b2c-1e54-4cc4-99ef-917deacc62b5" class="GINGER_SOFTWARE_mark"><span id="d1ee8e0b-a182-47b3-ae3e-aec6e3c4d4d5" class="GINGER_SOFTWARE_mark"><span id="ba9813f9-adcb-456c-863f-3d8a1274aee2" class="GINGER_SOFTWARE_mark"><span id="5b2f2d5e-5493-4e91-9643-97dfa67ac4f2" class="GINGER_SOFTWARE_mark"><span id="7a99f861-ef68-4a9c-b209-c4cbf5c76989" class="GINGER_SOFTWARE_mark"><font>(</font></span></span></span></span></span></span></span></span><font>);“功能的内容,</font></font> <span id="0abff33e-9b19-4b81-88c6-351609db7406" class="GINGER_SOFTWARE_mark"><span id="2aa002db-1fa3-4426-a63f-58a77b803238" class="GINGER_SOFTWARE_mark"><span id="782a87f0-4def-4e77-848c-bb0f80df189c" class="GINGER_SOFTWARE_mark"><span id="2f8c8b2c-1e54-4cc4-99ef-917deacc62b5" class="GINGER_SOFTWARE_mark"><span id="d1ee8e0b-a182-47b3-ae3e-aec6e3c4d4d5" class="GINGER_SOFTWARE_mark"><span id="ba9813f9-adcb-456c-863f-3d8a1274aee2" class="GINGER_SOFTWARE_mark"><span id="5b2f2d5e-5493-4e91-9643-97dfa67ac4f2" class="GINGER_SOFTWARE_mark"><span id="7a99f861-ef68-4a9c-b209-c4cbf5c76989" class="GINGER_SOFTWARE_mark"><font></font></span></span></span></span></span></span></span></span><font></font></em><br><em><font><font>我发现我上传的文件被命名为:page_d03b042780c5071521366edc01e52d3d </font></font><span id="aecd5cd8-2164-490b-a4d3-879a54e22ce9" class="GINGER_SOFTWARE_mark"><span id="182bb827-5d4b-42f5-b5d0-6ff8171d3c42" class="GINGER_SOFTWARE_mark"><span id="d1dc8af8-e35d-433c-b93b-4e74c57fc598" class="GINGER_SOFTWARE_mark"><span id="4446587a-b876-4c0f-9f92-0c30b74ea723" class="GINGER_SOFTWARE_mark"><span id="33aa4f07-c280-4404-bb9a-d4aecfd54528" class="GINGER_SOFTWARE_mark"><span id="2af7e5e5-2933-4c40-9b40-51abe0e9f219" class="GINGER_SOFTWARE_mark"><span id="a3da4687-fb7d-4220-adb8-7939eeef033a" class="GINGER_SOFTWARE_mark"><span id="75efb129-ade2-4b2d-ba2b-e38743c1f894" class="GINGER_SOFTWARE_mark"><font><font>。</font></font></span></span></span></span></span></span></span></span> <font><font> XRDS + XML </font><span id="60948e07-2cf5-4122-a833-0aef219698d3" class="GINGER_SOFTWARE_mark"><span id="e2787126-d253-4f0c-9089-7398b761fcf3" class="GINGER_SOFTWARE_mark"><span id="bff7926f-3e04-4c35-a9df-e028f9a56fd7" class="GINGER_SOFTWARE_mark"><span id="6bea52a7-9e26-4980-b550-24dd2371ff5e" class="GINGER_SOFTWARE_mark"><font>,而不是</font></span></span></span></span><font>被page_d03b042780c5071521366edc01e52d3d.php </font><span id="24c15c8d-354f-4237-86c3-087c5ce47a37" class="GINGER_SOFTWARE_mark"><font>?!“国在博客中Hibrahim。</font></span></font> <span id="60948e07-2cf5-4122-a833-0aef219698d3" class="GINGER_SOFTWARE_mark"><span id="e2787126-d253-4f0c-9089-7398b761fcf3" class="GINGER_SOFTWARE_mark"><span id="bff7926f-3e04-4c35-a9df-e028f9a56fd7" class="GINGER_SOFTWARE_mark"><span id="6bea52a7-9e26-4980-b550-24dd2371ff5e" class="GINGER_SOFTWARE_mark"><font></font></span></span></span></span><font></font><span id="24c15c8d-354f-4237-86c3-087c5ce47a37" class="GINGER_SOFTWARE_mark"><font></font></span></em></span></p></blockquote><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="528f9d50-1474-40c6-926e-32deb4141b7e" class="GINGER_SOFTWARE_mark"><font><font>检查</font></font></span><font><font> 3篇的要求,专家发现了问题的原因,在“内容类型”头!</font></font></span></p><p style="text-align: center; font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><a href="http://securityaffairs.co/wordpress/wp-content/uploads/2014/09/SQL-Injection-Yahoo-3.png" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold; background-color: white;">
 </a></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="048cea2e-5c55-4960-ae62-8ff80b977a81" class="GINGER_SOFTWARE_mark"><font><font>重命名 </font></font></span><font><font>的“内容类型”标题为“应用程序/ </font><span id="d87968df-9494-48e6-8516-04bbe31bf9c0" class="GINGER_SOFTWARE_mark"><font>PHP</font></span><font> “的问题得到了解决。</font></font> <span id="d87968df-9494-48e6-8516-04bbe31bf9c0" class="GINGER_SOFTWARE_mark"><font></font></span> <font></font></span></p><p style="text-align: center; font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><a href="http://securityaffairs.co/wordpress/wp-content/uploads/2014/09/SQL-Injection-Yahoo-4.png" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold; background-color: white;">
</a></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="048cea2e-5c55-4960-ae62-8ff80b977a81" class="GINGER_SOFTWARE_mark"><font><font>重命名 </font></font></span><font><font>的“内容类型”标题为“应用程序/ </font><span id="d87968df-9494-48e6-8516-04bbe31bf9c0" class="GINGER_SOFTWARE_mark"><font>PHP</font></span><font> “的问题得到了解决。</font></font> <span id="d87968df-9494-48e6-8516-04bbe31bf9c0" class="GINGER_SOFTWARE_mark"><font></font></span> <font></font></span></p><p style="text-align: center; font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><a href="http://securityaffairs.co/wordpress/wp-content/uploads/2014/09/SQL-Injection-Yahoo-4.png" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold; background-color: white;">
 </a></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="6c27030d-efeb-42d3-a658-b6e4a8082a77" class="GINGER_SOFTWARE_mark"><font><font>易卜拉欣</font></font></span><font><font>证明利用该漏洞进行SQL注入攻击,一个远程执行代码的可能性,他关闭了他的文章,解释如何获得目标服务器上的root访问权限。</font></font><font><font>黑客发现服务器内核进行了更新,最近一次于2012年,它是惊人的。</font></font><font><font>这是很简单的获得root权限与本地root权限到期的非内核打补丁的存在漏洞。</font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="73c0d06b-17ac-4bfd-aaf2-07cb14c16159" class="GINGER_SOFTWARE_mark"><font><font>下面的</font></font><span id="81fd163d-d43d-48b0-a49c-0c6b2255b104" class="GINGER_SOFTWARE_mark"><span id="648b9e0c-a8dc-41c7-88c2-401c7356081e" class="GINGER_SOFTWARE_mark"><span id="d490e3a7-f7a1-4b2c-8ff2-934beab0b0da" class="GINGER_SOFTWARE_mark"><span id="3cd5a2ce-e163-4e7b-84e3-b15f14b2f517" class="GINGER_SOFTWARE_mark"><font><font>时间线</font></font></span></span></span></span><font><font>的漏洞管理</font></font></span><font><font>:</font></font></span></p><blockquote style="margin-top: 20px; margin-bottom: 20px; margin-left: 20px; padding-left: 20px; border-left-width: 3px; border-left-style: solid; border-left-color: rgb(203, 202, 200); color: rgb(102, 102, 102); font-style: italic; line-height: 1.5em; font-family: Arial, Helvetica, sans-serif; font-size: 13px;"><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font class=""><font><font>2014年9月5日</font></font></font></strong><font class=""><font><font>至雅虎的初步报告扩展</font></font></font></em></p><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font><font>2014年9月6日</font></font></strong><font><font>雅虎证实漏洞存在</font></font></em></p><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font><font>2014年9月7日</font></font></strong><font><font>雅虎修复了漏洞</font></font></em></p><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font><font>2014年9月19日</font></font></strong><font><font>雅虎宣布我说,这个漏洞是没有资格获得奖励!</font></font></em></p></blockquote><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>让我以一个辩论的观察,怎么可能发现自2012年起的服务器打补丁?</font></font><font><font>为什么雅虎没有支付赏金这样的严重错误,即使它落入的范围之内?</font></font><font><font>雅虎是否考虑到SQLI RCE以根权限不是一个关键</font></font><span id="36dd8220-58ff-472e-b74d-84e9572f19d1" class="GINGER_SOFTWARE_mark"><font><font>的错误</font></font></span></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px; background-color: rgb(249, 247, 245);"><span class="GINGER_SOFTWARE_mark"><font><font><br></font></font></span></p><p style="margin-bottom: 10px; background-color: rgb(249, 247, 245);"><font style="font-family: Arial, Helvetica, sans-serif; font-size: 13px; line-height: 26.399999618530273px;"><font>来源:</font></font><span style="background-color: rgb(255, 255, 255); line-height: 26.399999618530273px;"><font face="Arial, Helvetica, sans-serif" size="2"><font><font>http://securityaffairs.co/wordpress/28475/hacking/yahoo-SQL注入,flaw.html</font></font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px; background-color: rgb(249, 247, 245);"><a title="http://www.linkedin.com/pub/pierluigi-paganini/b/742/559" href="http://www.linkedin.com/pub/pierluigi-paganini/b/742/559" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font></font></font></a></p>
</a></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="6c27030d-efeb-42d3-a658-b6e4a8082a77" class="GINGER_SOFTWARE_mark"><font><font>易卜拉欣</font></font></span><font><font>证明利用该漏洞进行SQL注入攻击,一个远程执行代码的可能性,他关闭了他的文章,解释如何获得目标服务器上的root访问权限。</font></font><font><font>黑客发现服务器内核进行了更新,最近一次于2012年,它是惊人的。</font></font><font><font>这是很简单的获得root权限与本地root权限到期的非内核打补丁的存在漏洞。</font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><span id="73c0d06b-17ac-4bfd-aaf2-07cb14c16159" class="GINGER_SOFTWARE_mark"><font><font>下面的</font></font><span id="81fd163d-d43d-48b0-a49c-0c6b2255b104" class="GINGER_SOFTWARE_mark"><span id="648b9e0c-a8dc-41c7-88c2-401c7356081e" class="GINGER_SOFTWARE_mark"><span id="d490e3a7-f7a1-4b2c-8ff2-934beab0b0da" class="GINGER_SOFTWARE_mark"><span id="3cd5a2ce-e163-4e7b-84e3-b15f14b2f517" class="GINGER_SOFTWARE_mark"><font><font>时间线</font></font></span></span></span></span><font><font>的漏洞管理</font></font></span><font><font>:</font></font></span></p><blockquote style="margin-top: 20px; margin-bottom: 20px; margin-left: 20px; padding-left: 20px; border-left-width: 3px; border-left-style: solid; border-left-color: rgb(203, 202, 200); color: rgb(102, 102, 102); font-style: italic; line-height: 1.5em; font-family: Arial, Helvetica, sans-serif; font-size: 13px;"><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font class=""><font><font>2014年9月5日</font></font></font></strong><font class=""><font><font>至雅虎的初步报告扩展</font></font></font></em></p><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font><font>2014年9月6日</font></font></strong><font><font>雅虎证实漏洞存在</font></font></em></p><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font><font>2014年9月7日</font></font></strong><font><font>雅虎修复了漏洞</font></font></em></p><p style="font-size: 1em; margin-bottom: 10px;"><em style="background-color: white;"><strong><font><font>2014年9月19日</font></font></strong><font><font>雅虎宣布我说,这个漏洞是没有资格获得奖励!</font></font></em></p></blockquote><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px;"><span style="background-color: white;"><font><font>让我以一个辩论的观察,怎么可能发现自2012年起的服务器打补丁?</font></font><font><font>为什么雅虎没有支付赏金这样的严重错误,即使它落入的范围之内?</font></font><font><font>雅虎是否考虑到SQLI RCE以根权限不是一个关键</font></font><span id="36dd8220-58ff-472e-b74d-84e9572f19d1" class="GINGER_SOFTWARE_mark"><font><font>的错误</font></font></span></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px; background-color: rgb(249, 247, 245);"><span class="GINGER_SOFTWARE_mark"><font><font><br></font></font></span></p><p style="margin-bottom: 10px; background-color: rgb(249, 247, 245);"><font style="font-family: Arial, Helvetica, sans-serif; font-size: 13px; line-height: 26.399999618530273px;"><font>来源:</font></font><span style="background-color: rgb(255, 255, 255); line-height: 26.399999618530273px;"><font face="Arial, Helvetica, sans-serif" size="2"><font><font>http://securityaffairs.co/wordpress/28475/hacking/yahoo-SQL注入,flaw.html</font></font></font></span></p><p style="font-size: 13px; margin-bottom: 10px; font-family: Arial, Helvetica, sans-serif; line-height: 26.399999618530273px; background-color: rgb(249, 247, 245);"><a title="http://www.linkedin.com/pub/pierluigi-paganini/b/742/559" href="http://www.linkedin.com/pub/pierluigi-paganini/b/742/559" target="_blank" style="text-decoration: none; color: rgb(66, 101, 167); font-weight: bold;"><font><font></font></font></a></p> |
|